“Security in cyber space should be one of the main cornerstones of economic prosperity in Iceland, resting on a foundation of sophisticated awareness of security issues and legislation.” —Icelandic National...


“Security in cyber space should be one of the main cornerstones of economic prosperity in Iceland, resting on a foundation of sophisticated awareness of security issues and legislation.” —Icelandic National...
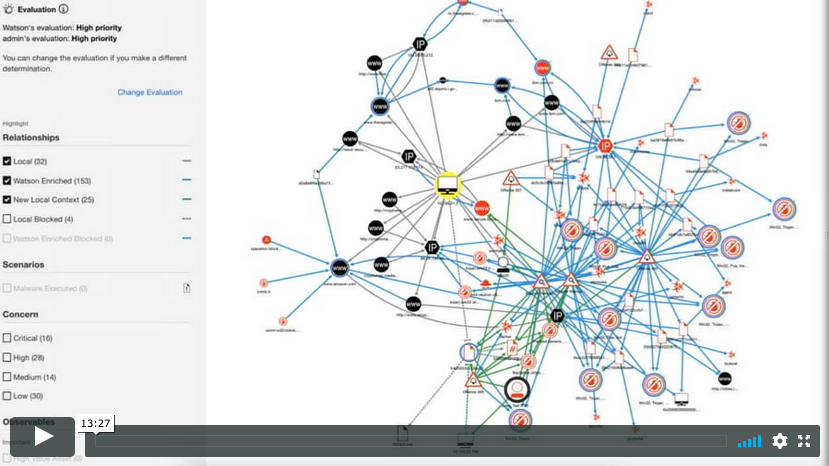
This case study examines how one Artificial Intelligence (AI) security software team made the decision to abandon a core feature of the product – an interactive Knowledge Graph visualization deemed by prospective buyers as “cool,” “impressive,” and “complex” – in favor of one that its users –...
Information Technology (IT) professionals are racing to keep up with cyber-security threats in the workplace. But, as any cyber-security expert will tell you, security technology is only as good as the people who use it. And, people are a mystery to most cyber-security professionals making them...