“Security in cyber space should be one of the main cornerstones of economic prosperity in Iceland, resting on a foundation of sophisticated awareness of security issues and legislation.” —Icelandic National...


“Security in cyber space should be one of the main cornerstones of economic prosperity in Iceland, resting on a foundation of sophisticated awareness of security issues and legislation.” —Icelandic National...
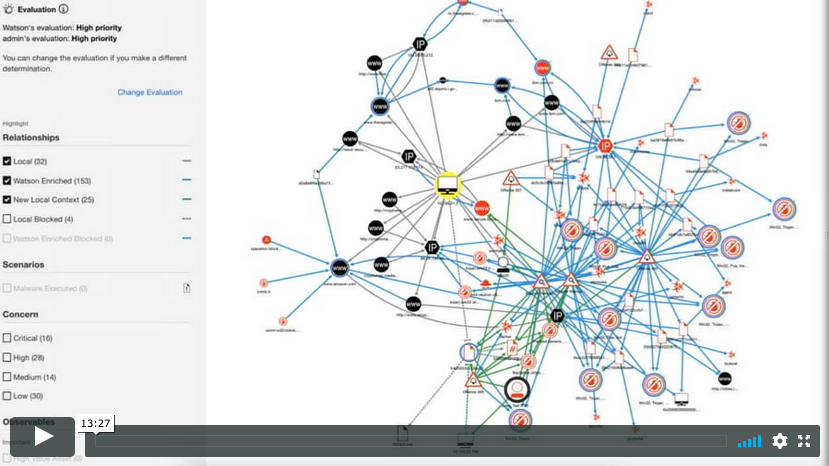
This case study examines how one Artificial Intelligence (AI) security software team made the decision to abandon a core feature of the product – an interactive Knowledge Graph visualization deemed by prospective buyers as “cool,” “impressive,” and “complex” – in favor of one that its users –...
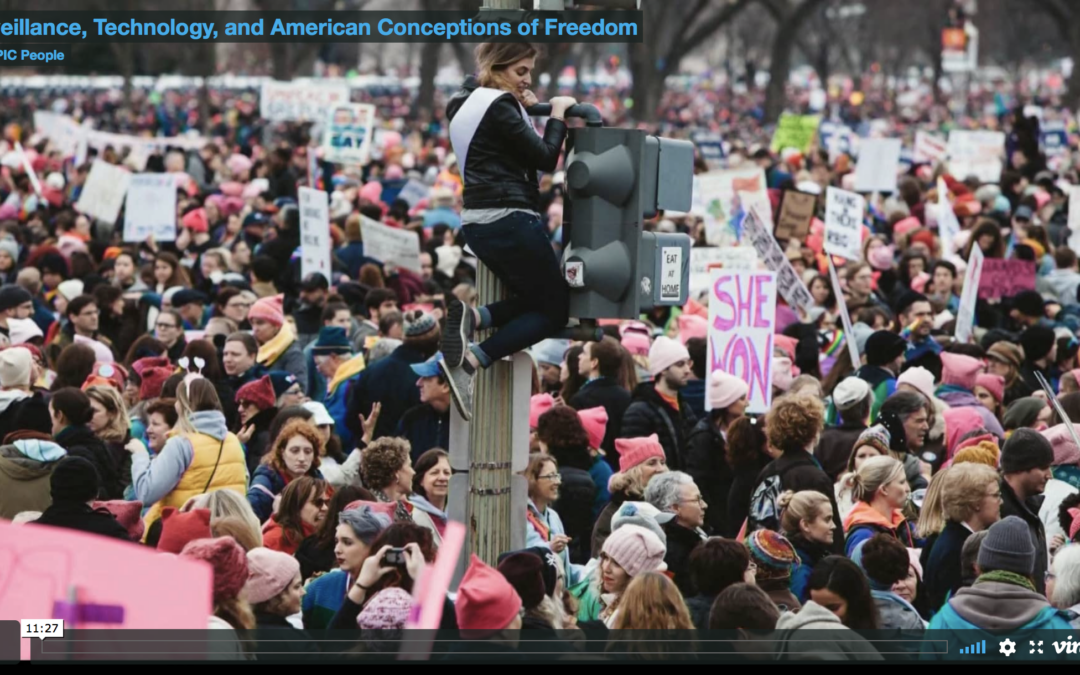
This paper traces the role of ideology in shaping the beliefs and situated knowledge used by information technology and security managers to make sense of and justify systems of surveillance they oversee. In particular, the analysis explores the role of the contested meanings of the ideology of...

Professional and organizational attention in recent years to what ethnographers can and cannot disclose as part of their research accounts has extended the range and relevance of concerns pertaining to the relation between investigators and those they study. When researchers are working under...
PechaKucha Presentation How can a researcher adapt to the lack of agency in secure environments? HM Inspectorate of Prisons in the UK published in 2012 a thematic report about the use of the “person escort record” (PER) with detainees at risk of self-harm, highlighting the high number of deaths in...

PechaKucha—Paradoxical thinking can reveal complex emotions and beliefs, even self-contradictory behaviors. It can also provide a gateway to the socio-cultural forces that underpin a topic. In a project on IT security, we encountered a participant whose paradoxical beliefs influenced his approach...